In today’s highly connected digital landscape, managing your cybersecurity is not just a recommendation — it’s an absolute necessity. One of the key tools to help users safeguard their devices and data is a dedicated security account. Total Defense Login These accounts offer users the ability to manage antivirus protection, review threats, set custom security preferences, and stay on top of updates and renewals — all from a central dashboard.
In this extensive guide, we will walk through every major aspect of using a cybersecurity account, focusing on how to set it up, navigate it confidently, manage your devices, Login Total Defense configure settings, troubleshoot common issues, and get the most value from the features offered. Whether you’re a new user or someone looking to deepen your understanding, this guide aims to make managing your cybersecurity simple and accessible.

Why Managing Your Cybersecurity Account Matters
Before diving into the detailed steps, Login Total Defense it’s essential to understand why taking control of your cybersecurity account is important.
Your cybersecurity software is only as effective as the way you manage it. By using the online account, you gain:
- Centralized Control: Manage all devices, settings, subscriptions, and updates in one place.
- Improved Security Posture: Set preferences, monitor threats, and take action faster.
- Easy Renewal and Upgrades: Stay ahead of expirations or software improvements.
- Real-Time Monitoring: Get immediate notifications about detected threats or system issues.
- Flexible Access: Manage your account from any device, anywhere, anytime.
Neglecting to use these account tools can lead to outdated protection, unmanaged devices, or even unnoticed security breaches.
Setting Up Your Account: The First Steps
To begin using your account, you must first complete a straightforward setup process.
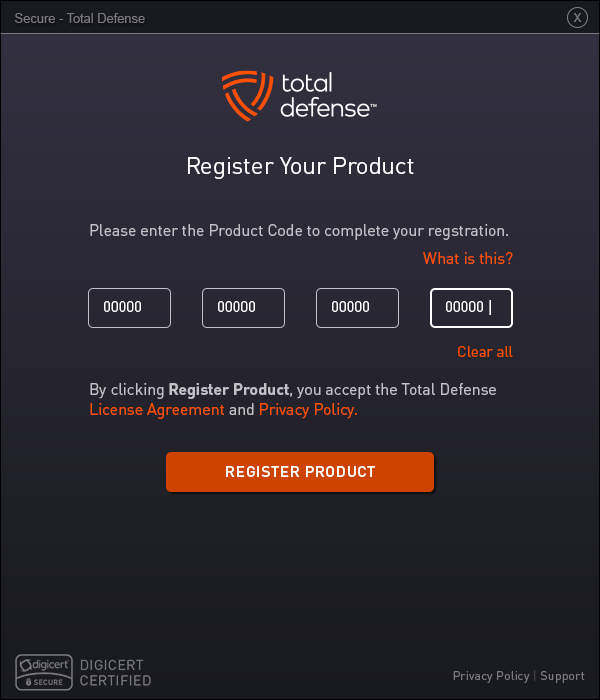
Register Your Account
Start by creating an account on the security provider’s website or through the software interface. Typically, this requires:
- Providing a valid email address.
- Creating a strong, unique password (combining uppercase, lowercase, numbers, and symbols).
- Agreeing to terms of service and privacy policies.
After registration, you’ll likely receive a confirmation email. Make sure to verify your email to activate the account fully.
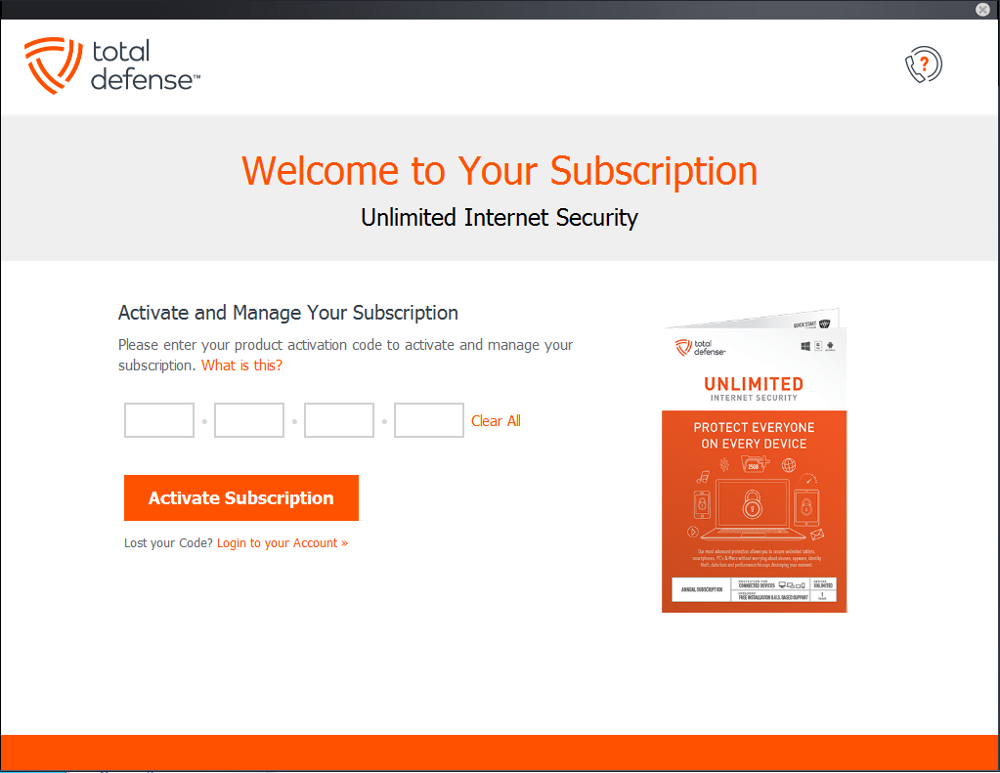
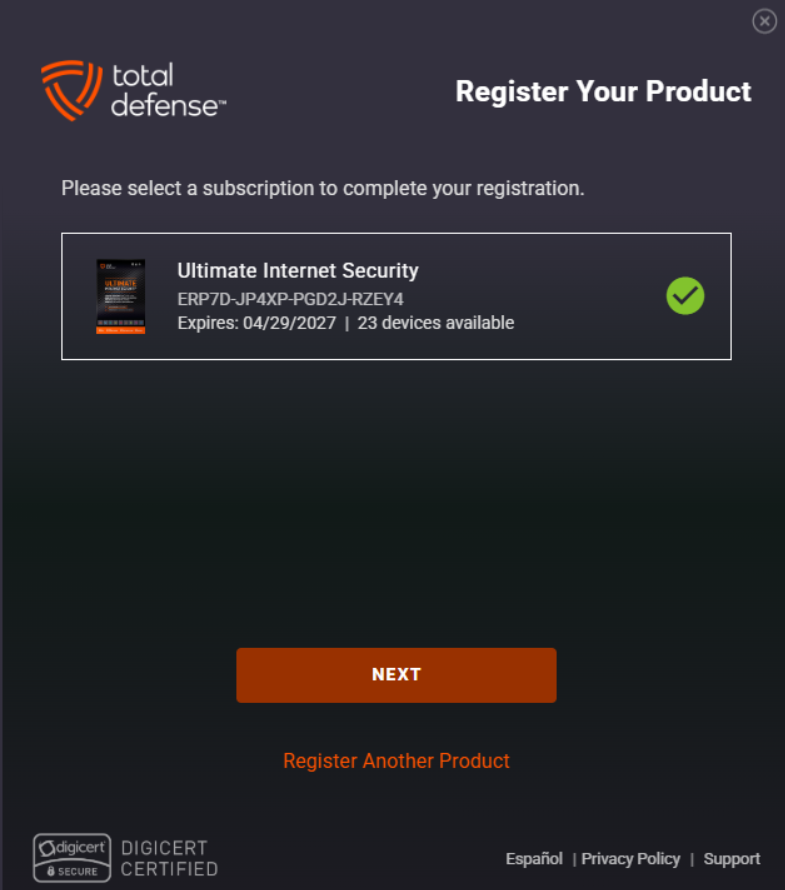
Link Your Subscription
If you purchased a subscription separately (such as from a retailer or partner site), you’ll need to link it to your account. This often involves entering a product key or activation code provided at the time of purchase.
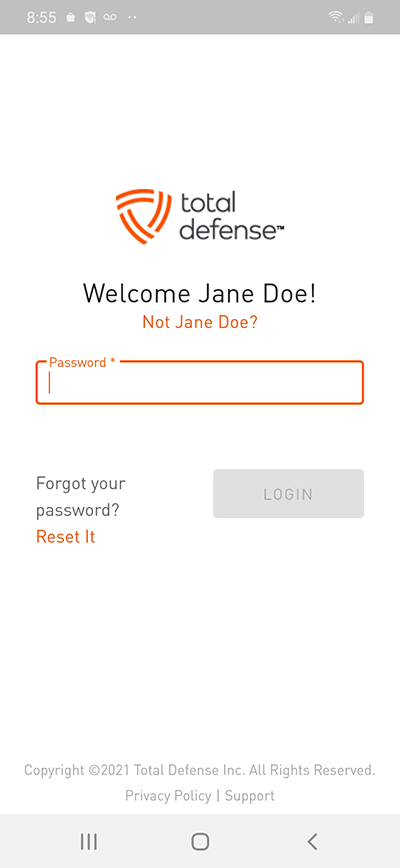
Logging In to Your Account
Once your account is set up and activated, logging in is straightforward.
- Visit the official website or open the desktop/mobile app.
- Enter your registered email address and password.
- Complete any additional authentication (such as two-factor verification, if enabled).
It’s recommended to enable two-factor authentication for added protection, which usually involves receiving a code on your phone or email each time you log in.
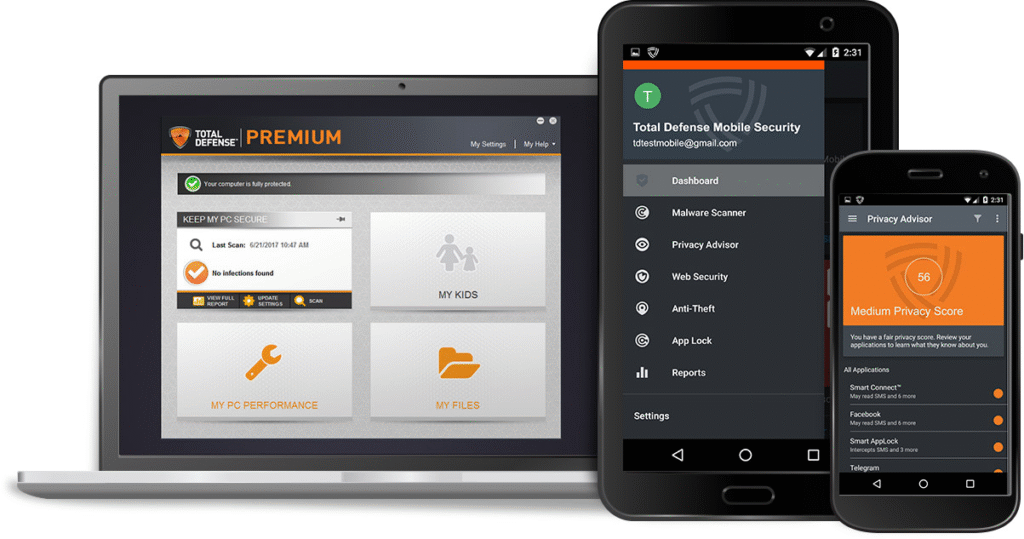
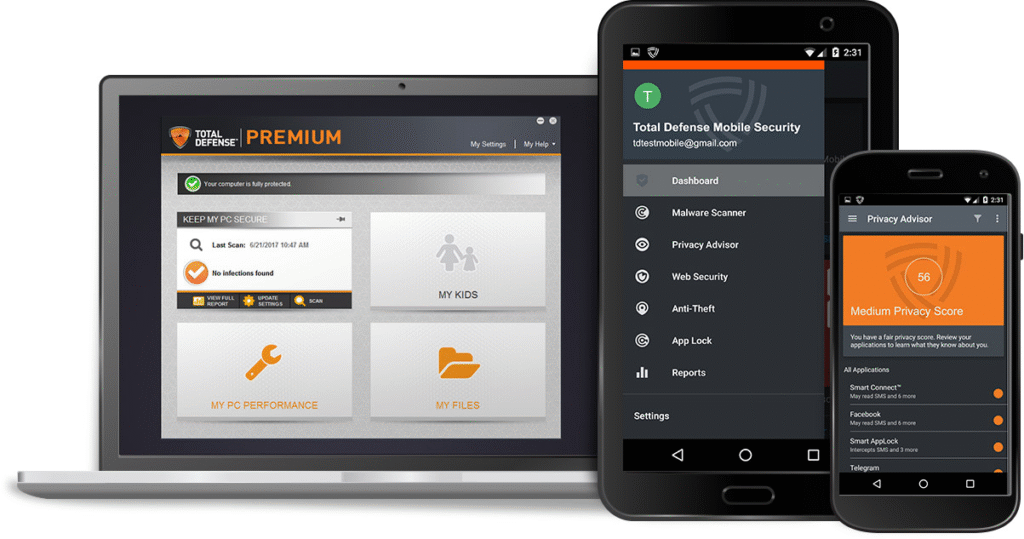
Navigating the Dashboard
After logging in, you’ll land on the account dashboard. Total Defense Login This is the central hub where you can monitor, manage, and customize your cybersecurity settings. Let’s break down the key sections typically found in the dashboard.
Devices Overview
Here, you can view Login Total Defense all devices linked to your account — computers, tablets, smartphones, and sometimes even smart home devices. You can:
- See which devices are actively protected.
- Check the security status of each device (e.g., last scan, last update).
- Add or remove devices as needed.
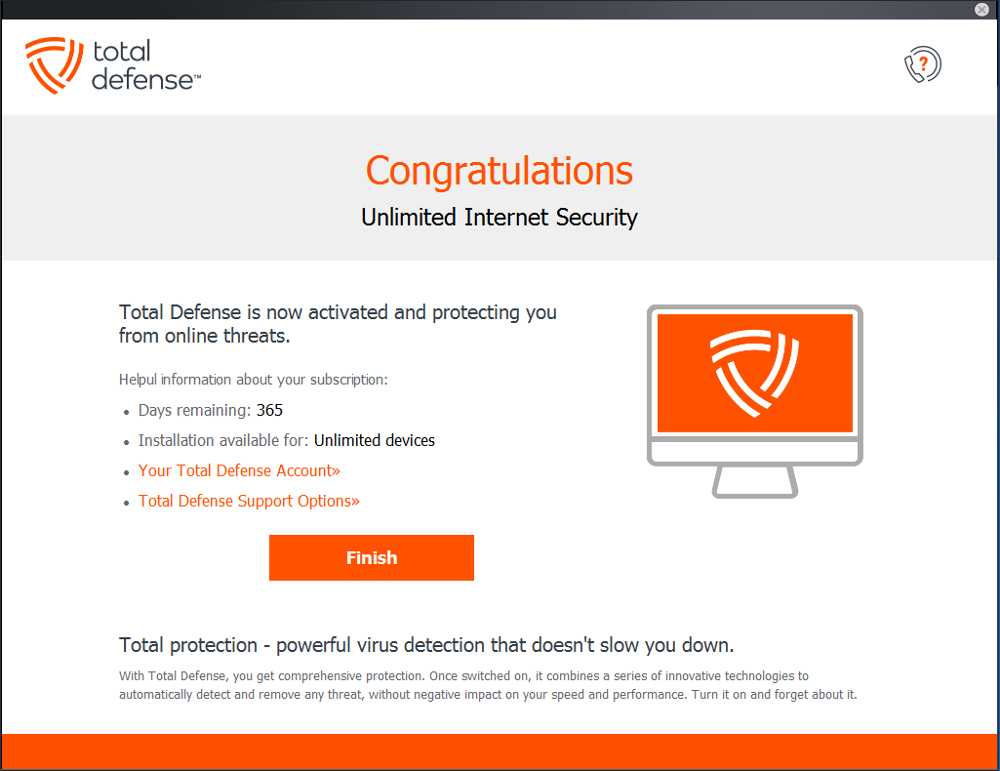
Subscription and Licensing
This section displays information about your active subscription, such as:
- Remaining validity period.
- Plan details (number of licenses, features included).
- Options to renew, upgrade, or extend your subscription.
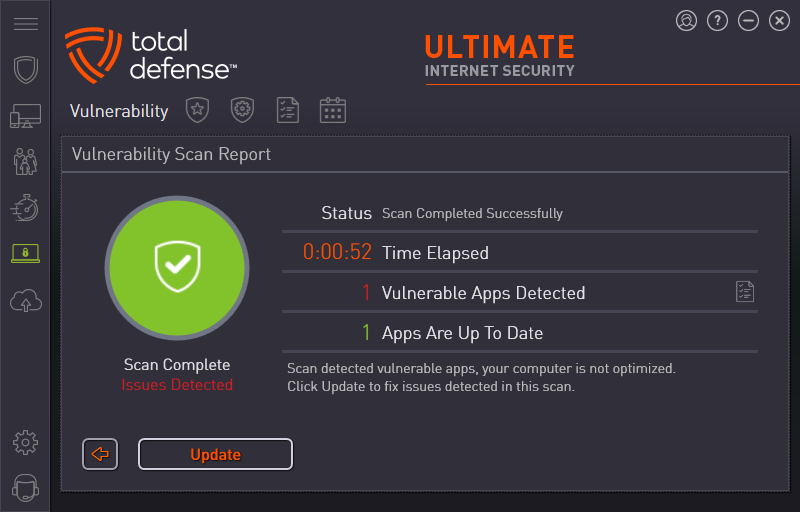
Security Settings
This is where you manage your protection preferences, including:
- Real-time scanning.
- Scheduled scans.
- Firewall rules.
- Web protection (anti-phishing, anti-malware, etc.).
- Parental controls or app restrictions.
Notifications and Alerts
Your account will alert you about detected threats, Total Defense Login software updates, subscription renewals, and other important events. Keeping an eye on notifications ensures you’re always informed about the security of your devices.
Adding and Managing Devices
An essential part of managing your account is ensuring all your devices are protected.
Adding a New Device
To add a device:
- Go to the “Devices” section of your account.
- Select “Add Device” and choose the appropriate platform (Windows, macOS, Android, iOS).
- Follow the prompts to download and install the software on the new device.
- Log in using your account credentials on the device to link it.
Removing a Device
If you no longer use a device or have replaced it, it’s wise to remove it from your account:
- Navigate to the “Devices” section.
- Select the device you want to remove.
- Confirm removal to free up a license and improve account security.

Customizing Your Protection
Customizing security settings allows you to tailor your defenses to your needs.
Real-Time Scanning
Ensure that real-time scanning is enabled so that threats are detected the moment they appear on your system.
Scheduled Scans
Set up daily, weekly, or monthly scans depending on your usage habits. More frequent scans are advisable if you frequently download files or browse unfamiliar sites.
Firewall Settings
If your plan includes a firewall, customize it to control what network traffic is allowed or blocked. Advanced users may set custom rules based on applications or ports.
Parental Controls
For families, use parental controls to manage what children can access online. Set age-appropriate filters, monitor usage, and schedule screen time limits.
Updating Software and Definitions
Keeping your software and virus definitions up to date is crucial for maximum protection.
- Enable automatic updates whenever possible.
- Regularly check your account dashboard for available software upgrades.
- Manually trigger updates if automatic updates are delayed or turned off.
Renewing and Upgrading Your Subscription
Your account makes managing renewals simple.
Renewal Process
- Monitor the expiration date displayed in the “Subscription” section.
- Renew early to avoid lapses in protection.
- Select the plan that best fits your needs — sometimes discounted rates are available for early renewal or multi-year plans.
Upgrading
If you need additional features (such as expanded device coverage or premium tools), Total Defense Login upgrade directly through your account.
- Review available plans.
- Choose your preferred upgrade.
- Complete the payment process and apply the upgrade across your devices.
Troubleshooting Common Account Issues
Even the best software can encounter occasional problems. Login Total Defense Here’s how to handle common account-related issues.
Forgotten Password
- Use the “Forgot Password” link on the login page.
- Follow the prompts to reset your password via email.
- Choose a new, strong password you haven’t used before.
Account Lockouts
- Wait a short time if you’re locked out after multiple failed attempts.
- Reset your password or contact customer support if the issue persists.
Device Not Appearing
- Ensure the software is installed and running on the device.
- Log in with the correct credentials.
- Try reinstalling the software and re-linking the device.
Maximizing Account Security
To make your account as secure as possible:
- Enable Two-Factor Authentication: Adds a layer of protection against unauthorized access.
- Use Strong, Unique Passwords: Avoid reusing passwords from other accounts.
- Audit Device List Regularly: Remove devices you no longer own or recognize.
- Keep Contact Information Updated: Ensure you can receive security notifications promptly.
Getting Help When You Need It
If you encounter issues you can’t resolve, your account usually provides several support channels:
- Help Center or FAQ: Access documentation and guides directly through your account.
- Support Tickets or Live Chat: Reach out to customer support for personalized assistance.
- Community Forums: Engage with other users and share solutions.
Having access to support ensures you can resolve technical issues efficiently and continue protecting your devices.

Summary
Effectively managing your cybersecurity account is key to maintaining strong digital defenses. From registering and logging in, to adding devices, customizing settings, Total Defense Login keeping software updated, and troubleshooting issues, each step plays a role in building a secure online environment.
By staying engaged with your account, regularly reviewing your protection, and taking advantage of the available tools, Login Total Defense you ensure your devices and data remain safe from evolving cyber threats. With the right knowledge and a proactive approach, you can make the most of your cybersecurity software and enjoy peace of mind online.